Managing Azure AD App Keys
It used to be all you had to remember is when your site's SSL certificate was going to expire. Now we have certificates and client secrets that are used for all kinds of things in the cloud including for Azure AD apps. Consider this my public service announcement that you need to get better at managing these too. Failure is not an option, well unless you don't need things to run :)
This means either you become lazy and admit defeat by selecting never expire, or become a better person by giving in and getting a key rotation in the regular grooming of your cloud assets.
The problem all begins on the following screen when you setup your client secret. It's a little bit like mission impossible, this message will self-destruct. The key is only displayed once, and you can't change the expiration after creation. You can delete the key, and you can add new keys with different expirations. A simple manual rotation would be just creating another key, setting your app to use it before the other key is deleted or expires.
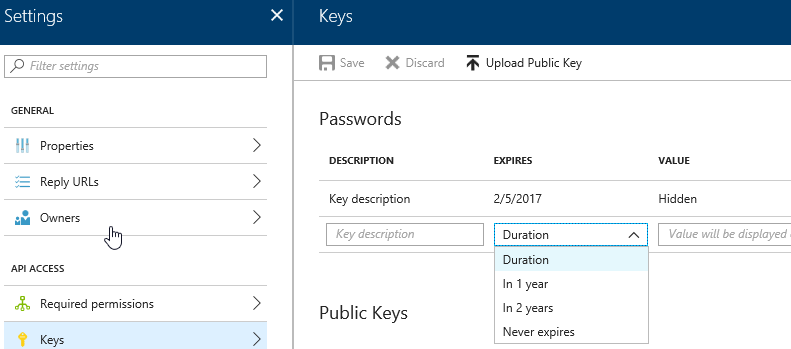
It's easy to get in trouble when creating the secret because you are excited to get the app to run, or deployed and select 1 or 2 years since you believe security is important. Then promptly forget to tell anyone or schedule a task prior to that expiration to rotate the keys. Don't worry; a reminder has been set for you in the way of a failing application.
Now is an excellent time to either personally or have your administrator do a key expiration audit. Go through each application in your Azure AD, review the keys and their expirations.
If your a little more advanced Key Vault in combination with Run Books can help you automate this, but even a manually process of rotation is better than a phone call late one night when it fails. You can read more about the key vault rotation here
I will be adding this reminder to the resources for my new training course we recently published on Building Custom Connectors for PowerApps and Flow. In the Hands-on Lab for that, it goes into details on how to use Azure AD auth with custom connectors, and this is a great way to practice your key management :)